Airgeddon is a multi-Bash network auditor capable of Wi-Fi jamming. This capability allows you to target and disconnect devices from a wireless network, all without needing to join it. Airgeddon runs on Kali Linux, and I will show you how to install, configure, and use the jamming functionalities on a small and inexpensive Raspberry Pi. When done correctly, it will deny service to a wireless network for up to several blocks.
This tool has gotten some attention lately, and I want to begin my series on Airgeddon by showing how electronic warfare techniques, such as jamming, can be used by hackers to disable devices such as wireless security cameras.
Electronic warfare is a pretty new concept. In the world of 2017, communications like GPS and Wi-Fi make more complex processes, and our way of life, possible. There are many ways to attack systems like drones (UAVs) or networked security cameras, but often their data connection is the most vulnerable.
Electronic warfare favors avoiding engaging these systems directly, instead choosing to disrupt and manipulate the data connection these automated devices rely on. Without a reliable connection, these devices often cease to function or revert to predictable, and exploitable, default behaviors.
The Electronic Warfare Approach for Hackers
Electronic warfare has been at the heart of some high-profile incidents.
The American military has invested heavily in automation with UAV programs, only to have adversaries like the Iranians develop tactics to disrupt these systems. By jamming the control signals of a top secret US spy drone while feeding it false GPS data, Iran was able to capture the drone by tricking it into landing in the wrong location.
The Russian military has also invested heavily in jamming and electronic warfareinnovation as a means of making American devices useless. Russia even demonstrated the ability to disable a US warship during a flight which knocked out the ship's power.
The majority of these powerful attacks are hardware-based and require devices that would be illegal or expensive to own. Fortunately, not all techniques rely on hardware. Today, we will focus on software-based attacks anyone with Kali Linux can employ.
The Wi-Fi DoS De-Authentication Attack
The "jamming" we are using, in this context, is one of many possible denial-of-service (DoS) attacks against a Wi-Fi network. Rather than overpowering the signal like a hardware jammer, a software jammer functions by forging network packets to continually request that all devices in range disconnect themselves. The process is described below.
This attack has the advantage of being effective against any Wi-Fi network, without needing to be authenticated to the network or know the password.
How to Jam a Wireless IP Security Camera
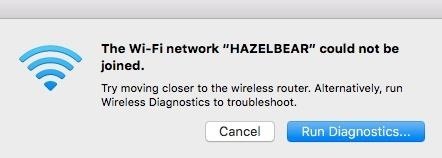
In our scenario today, we want to disable a wireless IP security camera connected to a network called "HAZELBEAR." Our target security camera relies on a Wi-Fi connection to stream video to a server. To disrupt that, we will kick all devices off of "HAZELBEAR" with Airgeddon. This will disable the camera from streaming video to whoever is watching or recording.
What You Need to Get Started
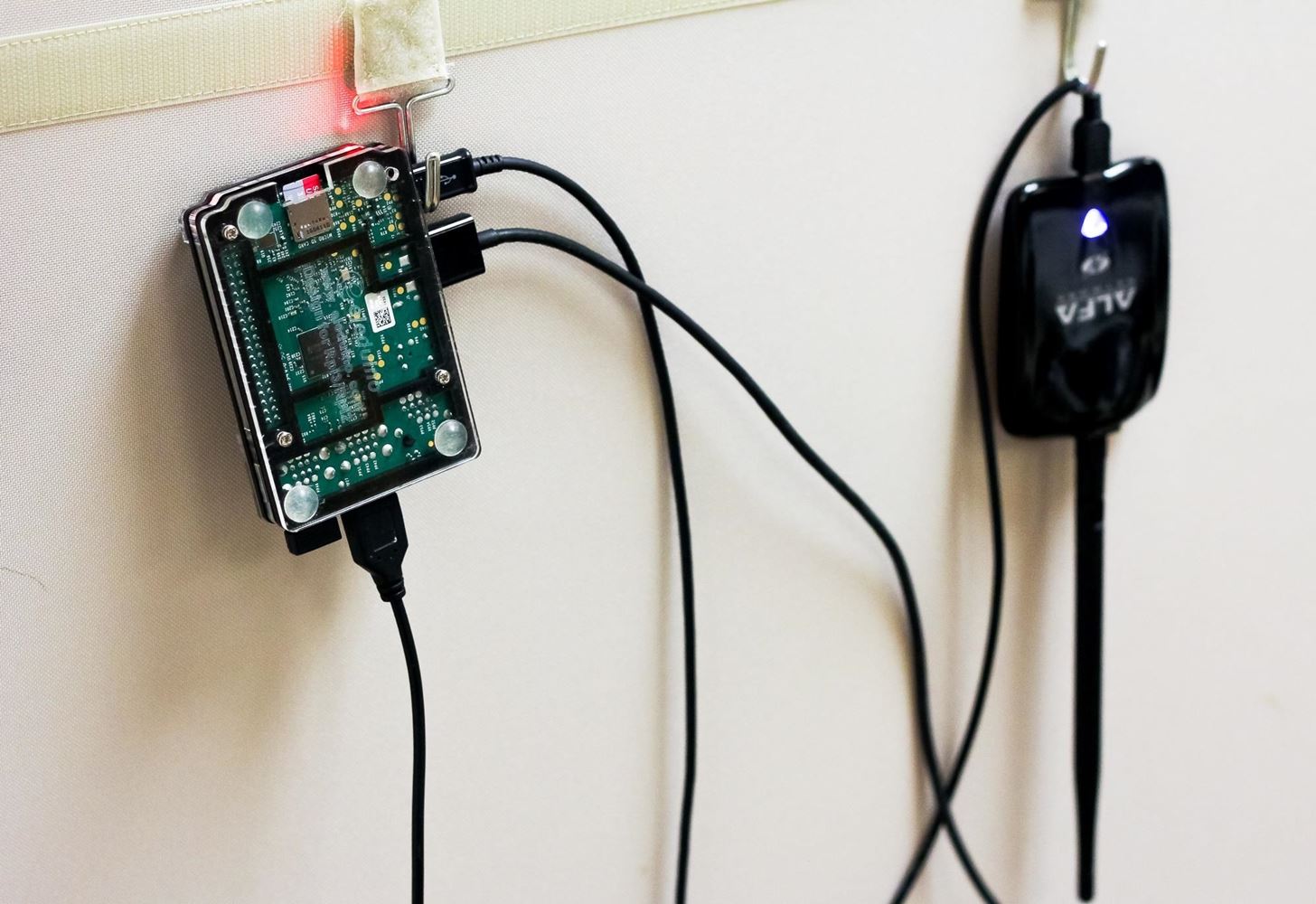
Airgeddon runs on Kali Linux. You can use an installation running on a virtual machine or on a $35 Raspberry Pi as I do in this demo to create a small portable option. If you'd like to run it on the Pi, check out our guide to setting up Kali Linux on the Raspberry Pi.
This tutorial will focus on installing Airgeddon on Kali Linux. Other operating systems it works on include Wifislax, Backbox, Parrot, BlackArch, and Cyborg Hawk. Since Airgeddon is a multi-Bash script and relies on opening multiple windows, it will not work over SSH. You should be connected via HDMI or VNC.
An Atheros AR9271, or another Kali-compatible wireless network adapter, must be capable of being put into monitor mode and packet injection, and you can find an excellent guide on Null Byte for selecting one below. The better the wireless adapter's range, the better your results will be.
Step 1Installing Airgeddon
First, let's check your configuration. Kali Linux must be fully updated running Kali Rolling to ensure system needs and dependencies are current.
Your wireless adapter capable of monitor mode must be plugged in and recognized by Kali, seen by typing iwconfig or ifconfig in a terminal window. Again, you must be using the Kali Linux GUI, not command line via SSH.
To install Airgeddon on Kali Linux, we will run the following commands in terminal to clone the git repository. Once downloaded, navigate to the newly downloaded Airgeddon folder, and start the script for the first time.
After entering the sudo bash command, Airgeddon will check for any updates or missing dependencies each time you run it. Some optional dependencies being marked as missing is fine for this tutorial. The fully updated version Kali Linux should have all of the essential tools.
Step 2Selecting Your Attack Interface
The next screen will give you a list of attached wireless cards. Select the attack interface by typing the number to the left of it, and you will be taken to the main menu.
Our interface is in managed mode, and we have not yet selected a target. Managed mode means the card cannot inject packets, which renders our attack impossible. We will need to put our card into "monitor mode" in the next step.
Step 3Setting Your Wireless Card to Monitor Mode
Ready the attack interface by typing "3" to select the third option, and follow the prompt to put your card into monitor mode. This allows us to inject forged packets which will convince target devices on the network to disconnect. Next, select option 4 to bring up the DoS attack menu.
Step 4Identifying the Target AP
We can now identify and select our target. Enter option 4 and press return to begin scanning for access points.
In this exercise, we will be attempting to find and disconnect clients from a network called HAZELBEAR. Press Ctrl-C to stop the scan once it has run for a minute or two to gather some networks. While this happens, a target list will appear. It is important to let this scan run long enough to find networks with attached clients, which are marked in the list with an asterisk.
When we have identified our target network and confirmed there are clients present, we will select the target network by typing its menu number. This will load the parameters, and enable the attack options menu.
Step 5Selecting Your Attack Option
Select your attack option by typing the number next to it. In this case, we will proceed with attack 5, a de-authentication / disassociation amok mdk3 attack. This uses the MDK3 took to send de-authentication and disassociation packets in "amoc mode." Other options are using the aireplay tool to spam de-authentication packets to targets, and overwhelming the target with WIDS / WIPS / WDS confusion attacks to flood the target with traffic.
Press enter to load the attack method you selected.
At this point, our target parameters are loaded. The attack is configured, and we are ready to launch the attack upon pressing enter.
You can now fire at will. When you press enter, a window will open showing the progress of the attack.
You will see this window open while the attack is active and running. At this point, all targets on the network should lose connection, and be unable to automatically reconnect.
If everything was done correctly, clients will not be able to connect to the network, and service is denied to not just the camera, but also the laptop viewing the video stream as well. The camera will be disabled, as well as any connected devices which depend on the wireless internet.
Warnings: DoS Is a Crime & Airgeddon Leaves Traces
Like any other DoS attack, this could be considered a crime depending on how you use it and if you have permission to audit the internet you are targeting. If not, be aware this attack will leave logs in the router that can be retrieved to determine the time and place of attack, the MAC address involved, and other information that can easily be used to identify you through nearby security cameras or cell tower logs.
This has been a high-level demonstration of jamming a target and applying electronic warfare techniques to hacking. Stay tuned for more!
By Rahul Developers










Always look forward for such nice post & finally I got you. Really very impressive post & glad to read this.
ReplyDeleteArchitects in Indore
Civil Contractors in Indore
Good luck & keep writing such awesome content.
ReplyDeleteVirgin Linseed Oil BP
flaxseed oil